:: Example email ::
2012-01-31 02:06:27 1Rrvn3-00041M-SX <= toby_campbell@gazetedun.net U=gztdny P=local S=1400 T="Hello"
2012-01-31 02:06:28 1RsDuq-0003tS-To <= toby_campbell@gazetedun.net U=gztdny P=local S=1400 T="Hello"
2012-01-31 02:06:28 1RsFBS-0002ZA-UM <= toby_campbell@gazetedun.net U=gztdny P=local S=1400 T="Hello"
Now you want know which is the email content (Header and Body) of the email sent from the user gztdny using the email toby_campbell@gazetedu.net
Open your ASSP WHM interface, click the "EXIM Queue Finder" , enter the email toby_campbell@gazetedu.net , and click "Search Queue" .
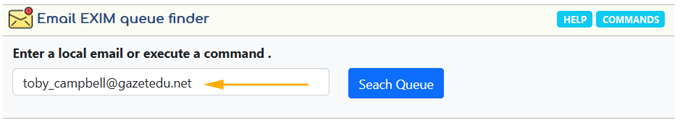
You should receive a result like this below
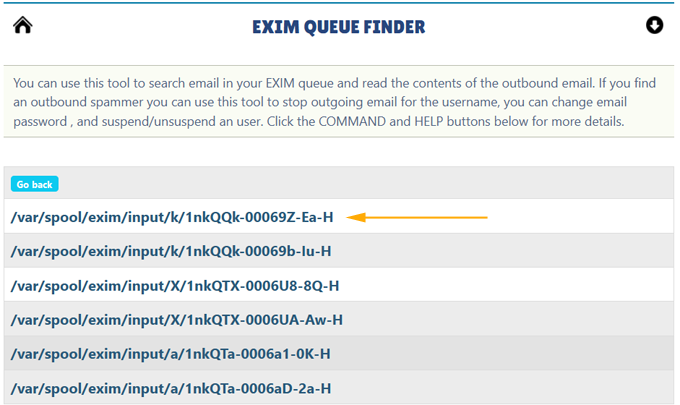
Click one of these email, for example
/var/spool/exim/input/k/1nkQQk-00069Z-Ea-H and you should be able to
read the email Header and Body of the email.
Let suppose that you found an email like this ..
[...] Received: from gztdny by dsh.unix1.info with local (Exim 4.69)
(envelope-from <brandon_cantrell@gazetedu.net>)
id 1RsDX9-002ulv-D1
for bevelcnc@aol.com; Tue, 31 Jan 2012 05:14:03 -0800
021T To: bevelcnc@aol.com
015 Subject: Hello
060F From: "Brandon Cantrell" <brandon_cantrell@gazetedu.net>
018 MIME-Version: 1.0
071 Content-Type: multipart/mixed; boundary="==5f01c2ee5634bd51a30c7737=="
052I Message-Id: <E1RsDX9-002ulv-D1@dsh.unix1.info>
038 Date: Tue, 31 Jan 2012 05:14:03 -0800
Content-Type: multipart/related; boundary="==5b840872ac47adf68f6f0cbe==";
type="text/html"
--==5b840872ac47adf68f6f0cbe==
Content-Type: text/html; charset="iso-8859-1"
Content-Transfer-Encoding: base64
CjxkaXY+Q2FuIHlvdSBiPFNQQU4gc3R5bGU9J2Zsb2F0OiByaWdodDsnPiBsbCA8L1NQQU4+ZWxp
ZXZlIGl0PyBZb3UncmUgbm90IGdvaW5nIHRvIHBheSBhIGxvdCBmb3IgcGlsPFNQQU4gc3R5bGU9
J2Zsb2F0OiByaWdodDsnPiBmYSA8L1NQQU4+bHMuIDxicj4gCk1ha2UgeW91ciBsaWZlIGhlYTxT
UEFOIHN0eWxlPSdmbG9hdDogcmlnaHQ7Jz4gdG4gPC9TUEFOPmx0aGllciBmb3IgYXBwcm9wcmlh
dGUgcHJpYzxTUEFOIHN0eWxlPSdmbG9hdDogcmlnaHQ7Jz4gbHAgPC9TUEFOPmUgaGVyZSE8L2Rp
dj4KPGgxPjxhIGhyZWY9Imh0dHA6Ly9yZWNhbGwuc2Fsa28ub3JnLnVhL2NhY2hlL3Ixd28zLmh0
bWwiPlZsYWc8U1BBTiBzdHlsZT0nZmxvYXQ6IHJpZ2h0Oyc+IHVzIDwvU1BBTj5yYSAkMC45MCBD
bGE8U1BBTiBzdHlsZT0nZmxvYXQ6IHJpZ2h0Oyc+IG1rIDwvU1BBTj5saXMgJDEuODA8L2E+PC9o
MT4K
in this case the spammer to make your life harder encoding the body using base64. Let we use a base64 decoder that can decode the base 64
content , you can use
this service for example.
Enter the base64 coded section and click "decode the data from a Base64 string
(base64 decoding)" and cick "convert source data"
ZXZlIGl0PyBZb3UncmUgbm90IGdvaW5nIHRvIHBheSBhIGxvdCBmb3IgcGlsPFNQQU4gc3R5bGU9
J2Zsb2F0OiByaWdodDsnPiBmYSA8L1NQQU4+bHMuIDxicj4gCk1ha2UgeW91ciBsaWZlIGhlYTxT
UEFOIHN0eWxlPSdmbG9hdDogcmlnaHQ7Jz4gdG4gPC9TUEFOPmx0aGllciBmb3IgYXBwcm9wcmlh
dGUgcHJpYzxTUEFOIHN0eWxlPSdmbG9hdDogcmlnaHQ7Jz4gbHAgPC9TUEFOPmUgaGVyZSE8L2Rp
dj4KPGgxPjxhIGhyZWY9Imh0dHA6Ly9yZWNhbGwuc2Fsa28ub3JnLnVhL2NhY2hlL3Ixd28zLmh0
bWwiPlZsYWc8U1BBTiBzdHlsZT0nZmxvYXQ6IHJpZ2h0Oyc+IHVzIDwvU1BBTj5yYSAkMC45MCBD
bGE8U1BBTiBzdHlsZT0nZmxvYXQ6IHJpZ2h0Oyc+IG1rIDwvU1BBTj5saXMgJDEuODA8L2E+PC9o
MT4K
You will receive following decoded section
Make your life hea<SPAN style='float: right;'> tn </SPAN>lthier for appropriate pric<SPAN style='float: right;'> lp </SPAN>e here!</div>
<h1><a href="http://recall.salko.org.ua/cache/r1wo3.html">Vlag<SPAN style='float: right;'> us </SPAN>ra $0.90 Cla<SPAN style='float: right;'> mk </SPAN>lis $1.80</a></h1>
which is an unsolicited message sent from user gztdny !
You can now get actions to stop the outgoing local spammer ; you may suspend user
gztdny or change password for email account toby_campbell@gazetedu.net or stop outgoing email for user gztdny.
All these actions can be done using the Email queue finder too ! Click here for more info.